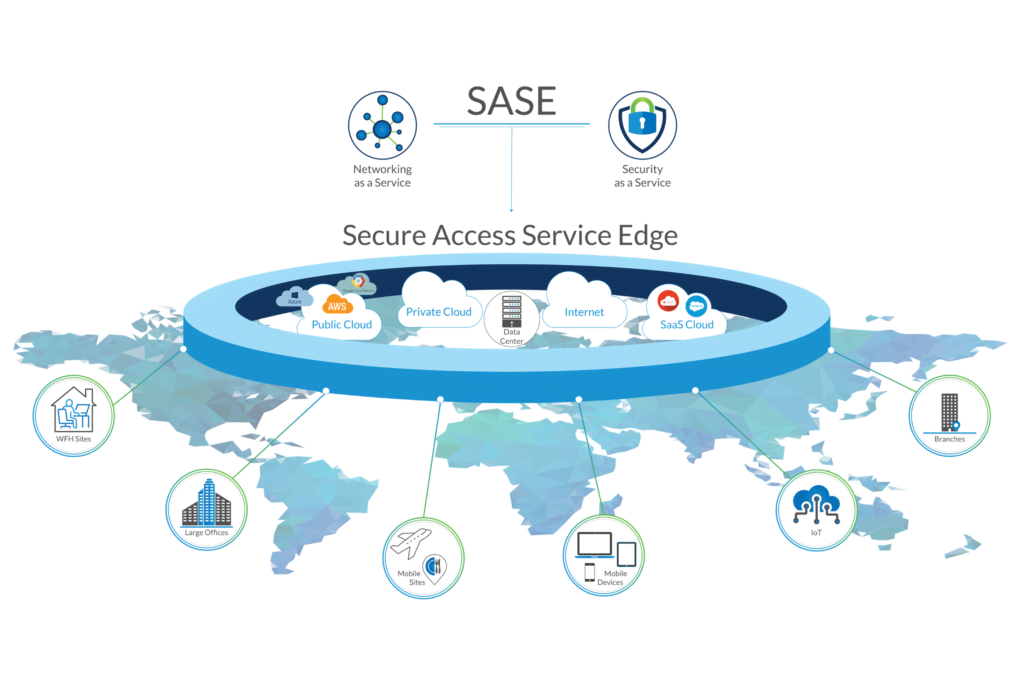
Every enterprise and MSP’s are aware of what SASE is, and the humongous power it has to adapt to the unprecedented cyber needs of the organization. The rapid rate at which cloud application usage is increasing, majority of users, devices and data are moving to a remote work environment. The key for an enterprise to survive in this challenging time is to adapt to a new model of network infrastructure built around SASE. The legacy network infrastructure needs to be abandoned quickly or else risk going obsolete in the next 5 years. According to a recent data published, 51% of CxO’s do not know what their industry will look like in 2023. Understanding the essence of cyber needs for your industry can be the margin between skyrocketing or going bankrupt.
How can an enterprise ensure the security of their data, employees, business model and their identity from being compromised ? The answer is “SASE, Secure Access Service Edge”.
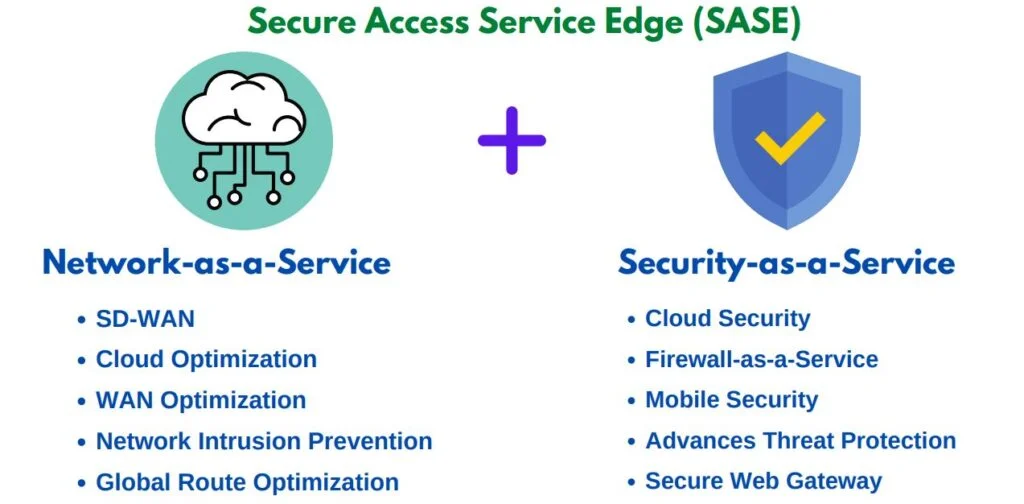
What does SASE provide for your organisation?
SASE is the integration of various cloud security solutions; notably Cloud Access Security Broker (CASB), Secure Web Gateway (SWG), and Zero Trust Network Access (ZTNA). The combined value of all these core functionalities into one single SASE model of architecture grants vital data and threat protection for an enterprise. The four-core offerings of SASE functionality are:
High Data Visibility
SASE offers enterprise high data visibility and monitoring at a granular level. Absence of a proper data visibility paradigm keeps the organization in the dark. Comprehensive visibility enables the organization to identify and regulate data patterns accordingly. This is a critical for an enterprise that needs demonstration of regulatory compliance.
Data Loss Prevention (DLP)
Data loss prevention policies are offered at the granular level by the SASE’s architecture model. DLP policies in SASE helps to identify sensitive data to protect that is at rest within the cloud’s SaaS environment and on – premise application. It is vital that confidential information does not leak and also prevention of exfiltration from the web is stopped.
Identity and Access Management (IAM)
SASE model offers a single sign-on (SSO) mode of authentication that serves as the sole point of authentication across all managed services and applications. Authenticating users is very vital step in creating a smart, intelligent and context-based security. It is a superior format of authentication than multi-factor authentication (MFA). IAM is crucial in protecting the identity of the users in an enterprise from malicious threats and sniffers trying to access accounts.
Unified Threat Management (UTM)
Organizations today must be able to adapt to the changing cyber requirements. The growing rate of cyber attack methods will only keep increasing along the way. For an enterprise, SASE offers a solid platform that blocks known and zero- day malware during any instance of upload, download or rest. Additionally, malicious web destinations are blocked preventing malware infections and phishing schemes of any sort. In case, there is an infiltration, either internal or external the process is stopped immediately preventing further leakage.
Secure Web Gateway (SWG)
Secure Web gateway solutions protect Web-surfing PCs from infection and enforce company policies. Also, a solution that filters unwanted software/malware from user-initiated internet traffic and enforces corporate and regulatory policy compliance. These gateways include URL filtering, malicious-code detection and application controls for popular Web-based applications. Native or integrated data leak prevention is also increasingly included.
Remote Browser Isolation (RBI)
RBI moves the execution of a user’s browser activity from the client device to a remote server — hosted on-premises or in the cloud. This protects against browser-based security exploits and provides a means of anonymous browsing and risk-free open Internet access. As the user browses the public Internet, the remote browser is isolated from the user’s physical endpoint and enterprise network. Therefore, any attacks on the remote web browsing session are constrained to the virtual environment. RBI also helps with data protection, especially in the case of unmanaged or untrusted devices being used to access confidential or sensitive information.
Is SASE the ultimate answer?
In the present-day individual solutions like CASB, ZTNA and SWG functioning alone don’t have much meaning for an organisation’s security. Industry demands require a compact and integrated solutions rather than a partial solution. Enterprise’s that are seeking to acquire SASE’s solution should consider these below points:
The expanding attack surfaces
The attack perimeter in the cyber industry has shown no sign of slowing down. Hackers are always out there trying to infiltrate an enterprise to get valuable information. There can be several internal and external causes that might put the organization in a vulnerable position. Even internal human error is a big concern for an enterprise. SASE offers services in a compact package unit like DLP, IAM, threat protection and many more.
Security budget
Microsoft (MSFT) announced on Wednesday that it will invest $20 billion over the next 5 years in cybersecurity, four times its previous investments of $1 billion per year to protect its services
SASE has been designed to fit exactly in this 2.4% category where you don’t need any expenditure on physical devices. Every thing is in a single cloud-oriented platform. SASE’s offering can be used to replace all the standalone tools easily.
As data is moving off-site and into the clouds beyond the touch of legacy security technologies like onsite firewalls. SASE’s platform and model is the ideal way to be an enterprise of the modern era with modern security tools.