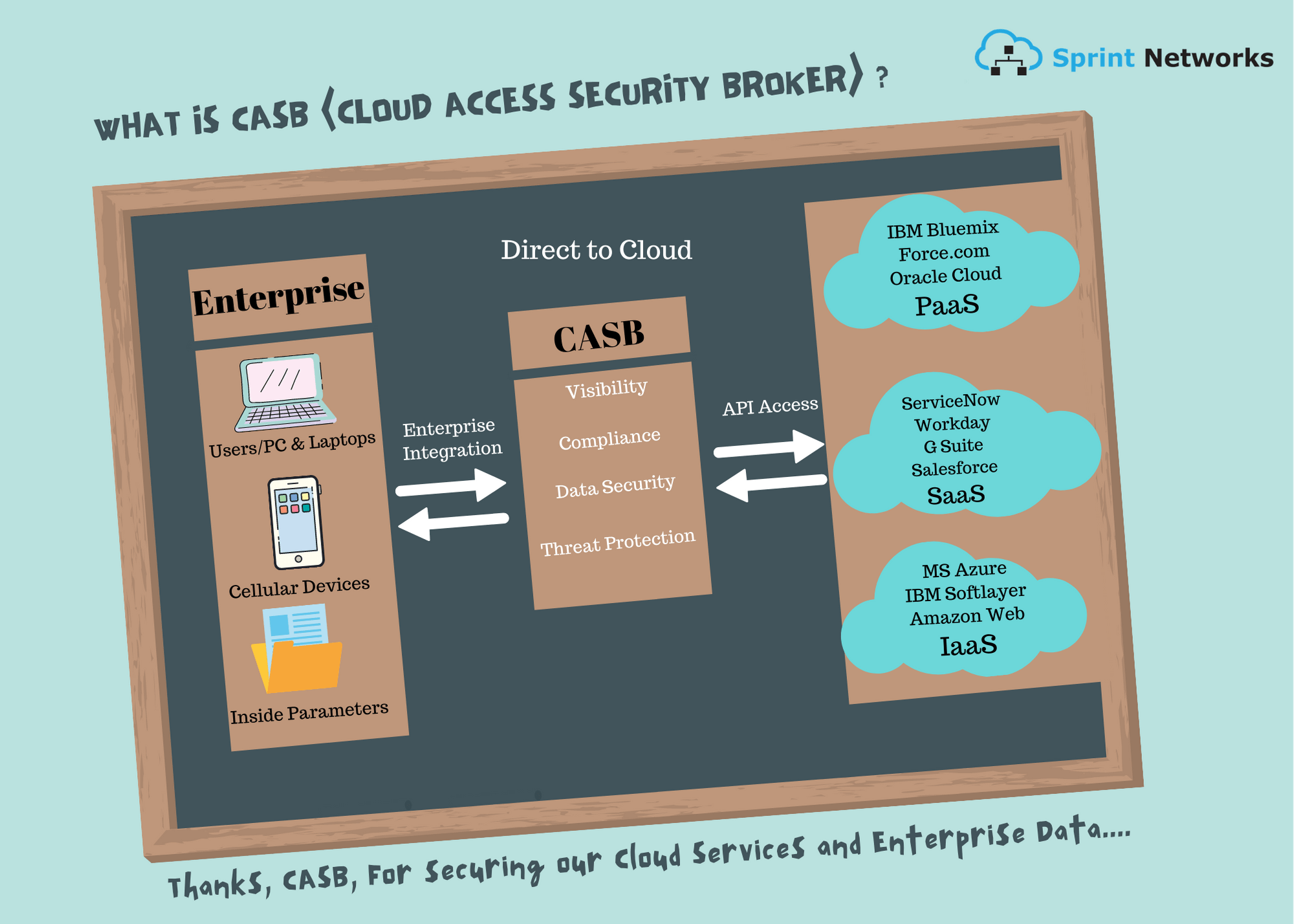
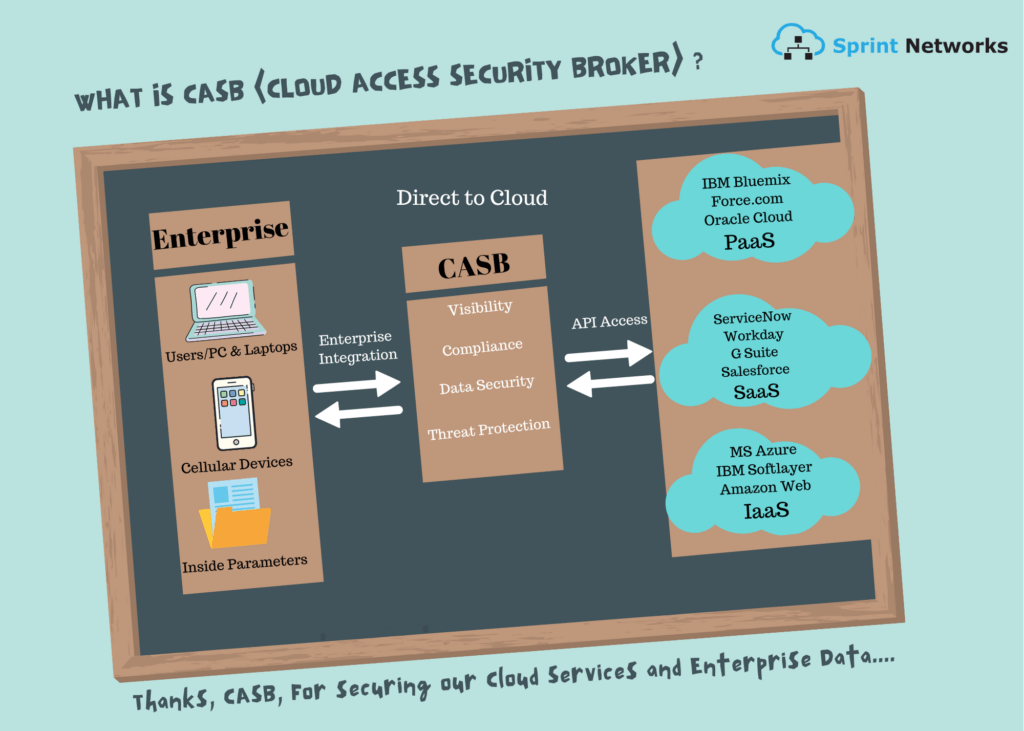
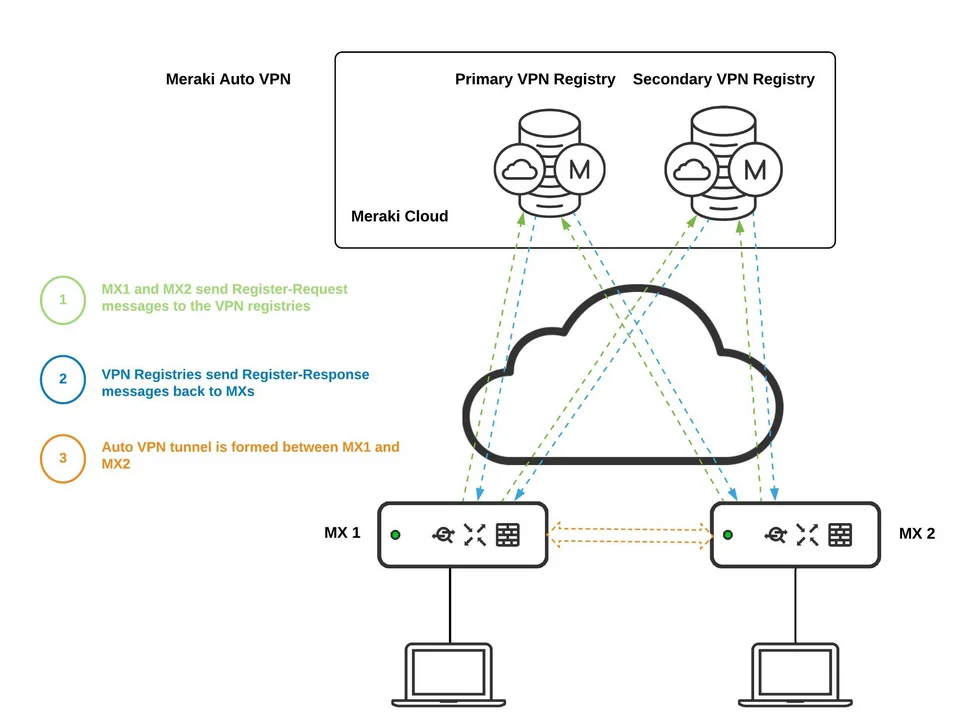
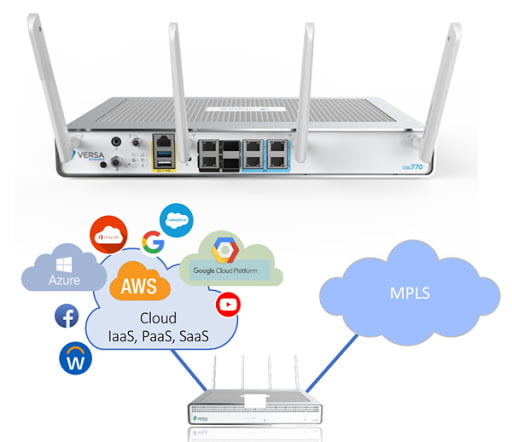
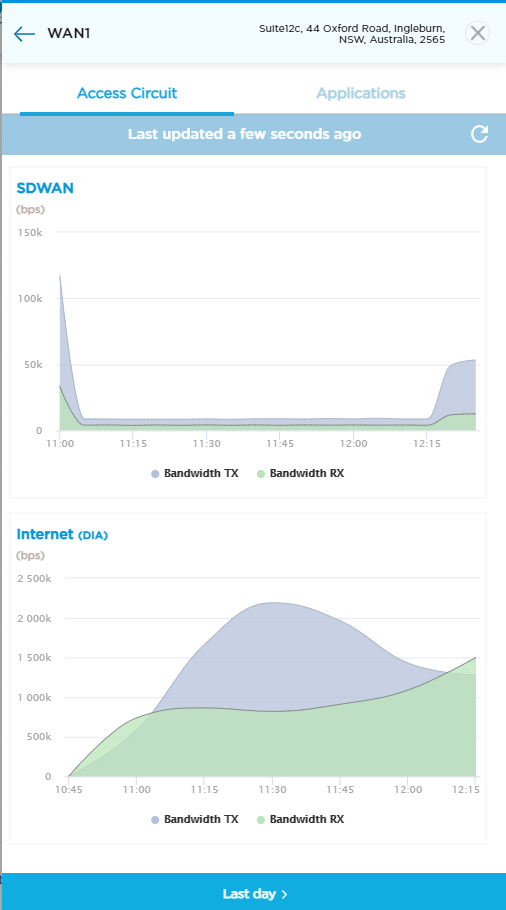
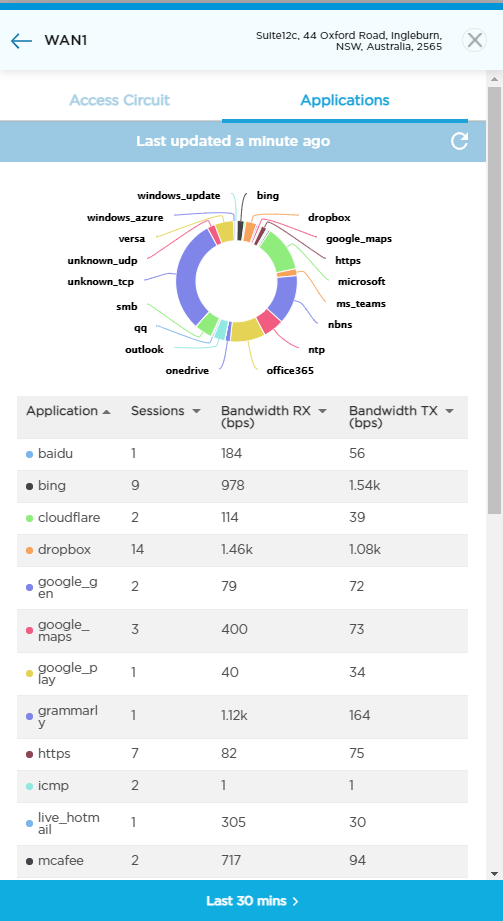
Where does CASB run?
CASB is found in both onsite premises and offsite in the cloud. But logically it sits between the user and the cloud acting as the middle man. Considering the physical location, a CASB has to be in either of the two places i.e. in a corporate data center or in the cloud itself. It depends on the user choice and as to what sort of network deployment they prefer. CASB can be used as a SaaS or hosted on a physical or virtual appliance.
How does CASB function?
CASB mainly operates in 2 ways. It can either be set up as a proxy i.e. Forward proxy or a Reverse proxy – or it can function in API mode using the cloud service providers APIs to maintain cloud access and apply security policies. Increasingly CASBs are becoming “mixed mode” or “multi-mode”.
Forward Proxy
All types of cloud applications can use forward proxy. All the data passes through forward proxy, but a requirement to that is the installations of self-signed certificates on every single device that accesses the proxy. In a large corporate organization, it can be difficult to deploy because of the distributed environment they might have. One with a large number of employees and owned mobile devices.
Reverse Proxy
A reverse method is much easier because it is accessible from any device, anywhere, without the need for special configuration or certificate installation. The backside to reverse proxy is that it can’t work with a client-server type application, which have hard coded hostnames.
API-Based Systems
API based systems are easy to be deployed in comparison to the other two. The drawback to this is that the range of cloud applications they can work fully is limited as not all applications can provide API support.
“Proxy or API architectures from CASB have different abilities to perform different actions, which have various implications for how that provider delivers the four pillars for a specific cloud service,” Gartner says.
In over the few years. Gartner expects many cloud service providers to have their own API.
One CASB may not be enough
The various capabilities of CASBs- forward proxy, reverse proxy, API based or multimode vary. CASB differs from each other as the development of each might differ at the mercy of the vendors who have developed it. Just because a CASB supports one application doesn’t mean it might support as much or to the extent of another CASB.
Choosing a CASB that supports the application an enterprise uses now, and are likely to use in the future might be a challenge. Mostly office apps like CRM, HR and ERP are generally well supported but industry specific apps e.g., healthcare industry might not be.
One of the advices handed out by Gartner is that,” be cautious when entering into long-term contracts. Build in flexibility as you may require more than one CASB or may need to change from a current provider to the one that supports your enterprise use case thoroughly.
CASB Market size
The CASB market size has grown by a significant number as the demands for cloud security and middle man data security rises. The CASB market is expected to grow from $3.4 billion in 2015 to $7.5 billion in 2020, with a compound growth rate of 17.6%.
The increasing adoption of cloud-based applications such as Office 365, Salesforce, Google Apps is a playing a major role in fueling the growth of CASB market.
More than dozens of CASB startups have been launched since 2010 and a number of major CASB vendors have been acquired by bigger players in IT security.
Major CASB vendors include:
·
Bitglass
·
Blue Coat (owned by Symantec)
·
CipherCloud
·
CloudLock (owned by Cisco)
·
Forcepoint (through Skyfence acquisition; owned by
Raytheon)
·
Microsoft (through Adallom acquisition)
·
Netskope
·
Skyhigh
Networks (acquired by McAfee)