How to run a Simple API using AWS Lambda
Serverless computing is becoming one of the hottest topics in IT industry. Traditional server-based solutions need massive investment on capex and opex cost, including building and running hardware and software systems as well as other service needs to run a datacentre. Especially for ad-hoc task, running a dedicated instance would involve additional operational overheads.
AWS Lambda is a serverless compute service that lets you run code without provisioning or managing servers, creating workload-aware cluster scaling logic, maintaining event integrations, or managing runtimes. While using Lambda, all you need is to provide code for the task, and it can be triggered by API gateway as well as other AWS services which are fully managed by AWS. You will only need to pay for what you have used. The model of pay-per-use makes FaaS, function-as-a-service, insanely cheap.
Without going to too deep in concepts, I will demonstrate a simple lab about how simple to run a RESTful API by using AWS Lambda.
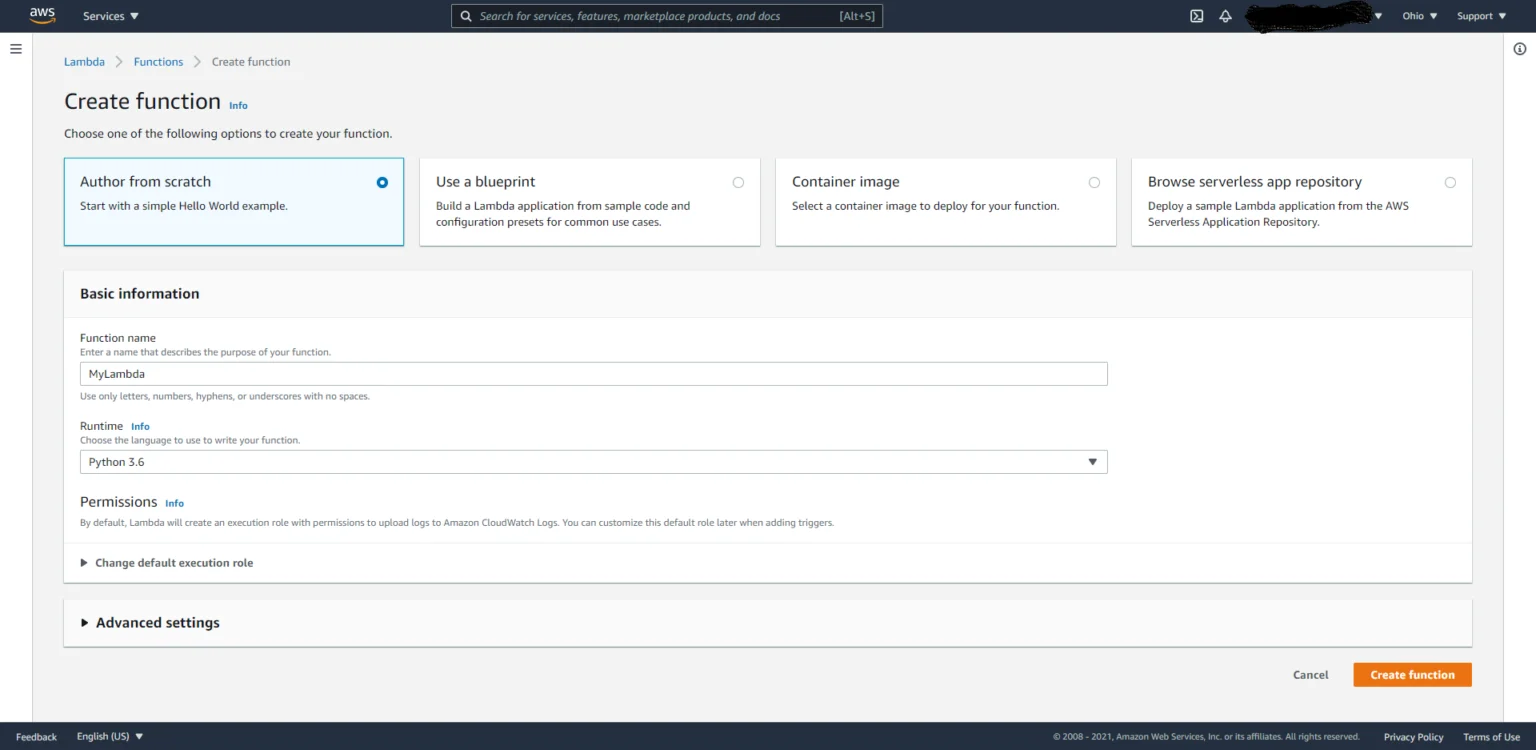
1. Enter the Lambda Console and create a Function
Blueprints provide example code to do some minimal processing. Most blueprints process events from specific event sources, such as Amazon S3, DynamoDB, or a custom application. In this lab, we will build a Lambda Function from scratch.
a. In the AWS Lambda console, select Create a Function
b. Select Author from scratch
c. Type in function name and runtime
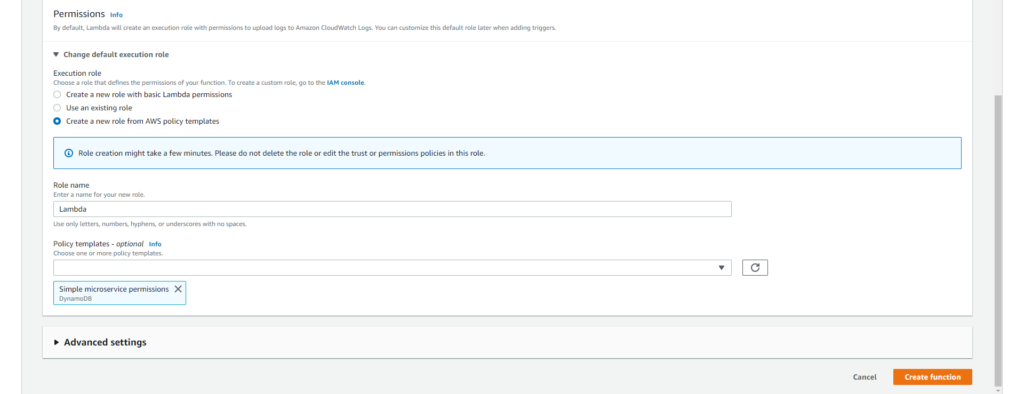
2. Configure permission for the Function
The lambda function needs right permissions to access the resources within your AWS account. You can create your own policy for Lambda or use pre-defined policy to attach.
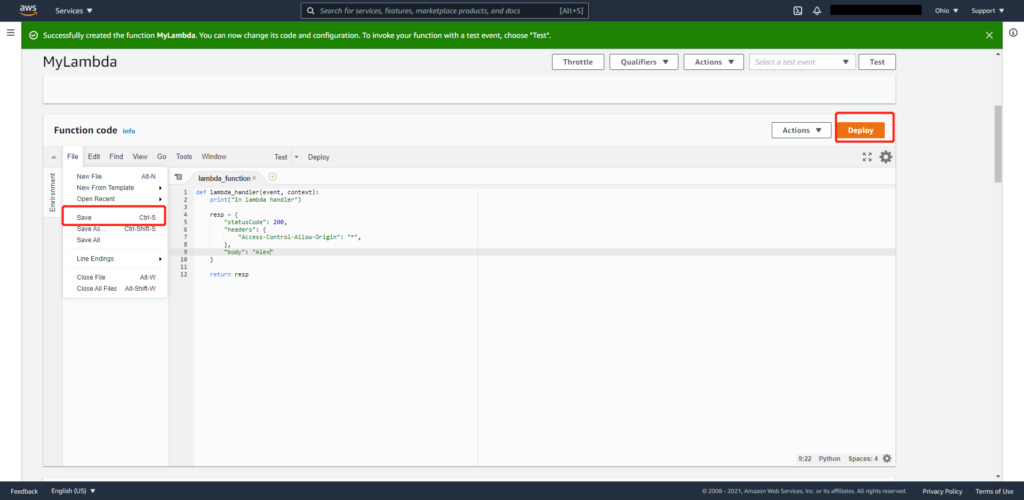
3. Input scripts and deploy the function
a. Upload the scripts as a ZIP file or paste it in.
b. navigate to File, and click Save to save the code for further editing.
c. Click the Deploy button to launch the function.
From here, the function has already been launched and ready to be used. You will need to add triggers to define when to use this function.
4. Using API Gateway as the trigger
Amazon API Gateway is a fully managed service that makes it easy for developers to create, publish, maintain, monitor, and secure APIs at any scale. In this case, APIs act as the “front door” for our Lambda function.
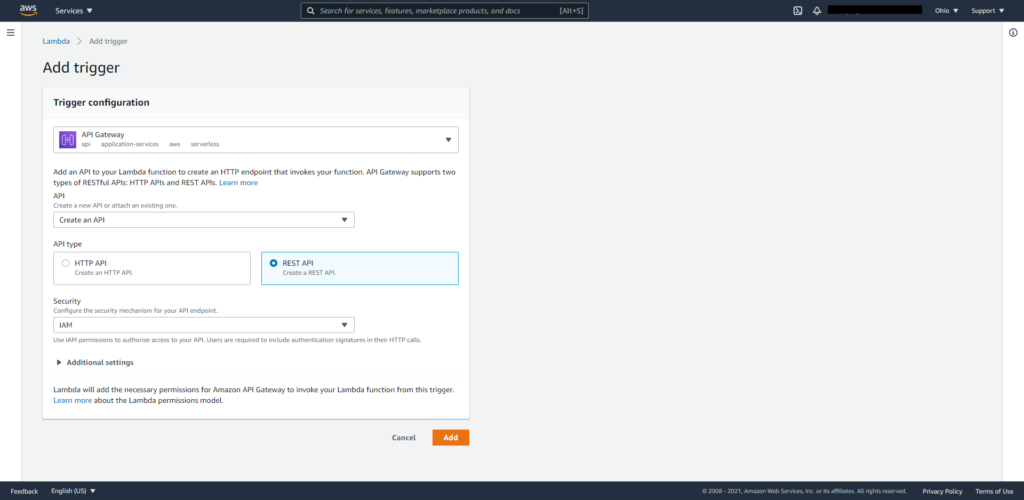
a. Click Add trigger in the function just created.
b. Type in the name and select REST API as the API Type.
c. Select the security mechanism for this function.
d. Click Add button to complete the trigger creation.
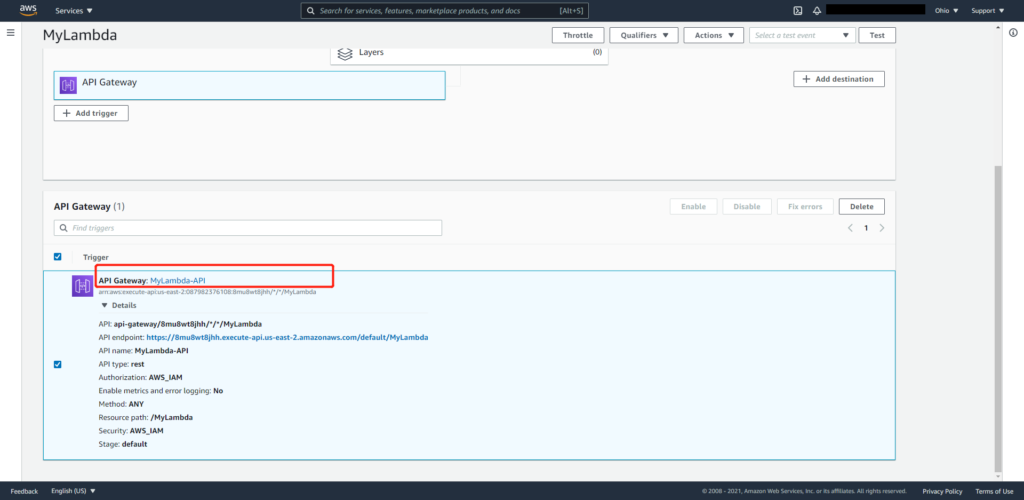
5. Editing trigger
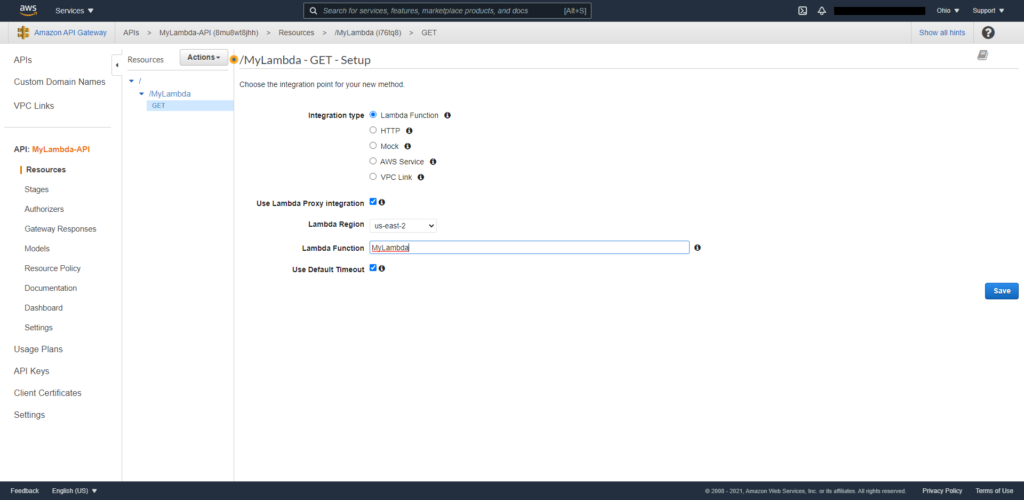
a. Create GET method for the trigger.
b. Click the GET method and select Lambda Function as the integration type.
c. Type the name of the function into the Lambda Function block.
d. Click Save to complete the trigger setting.
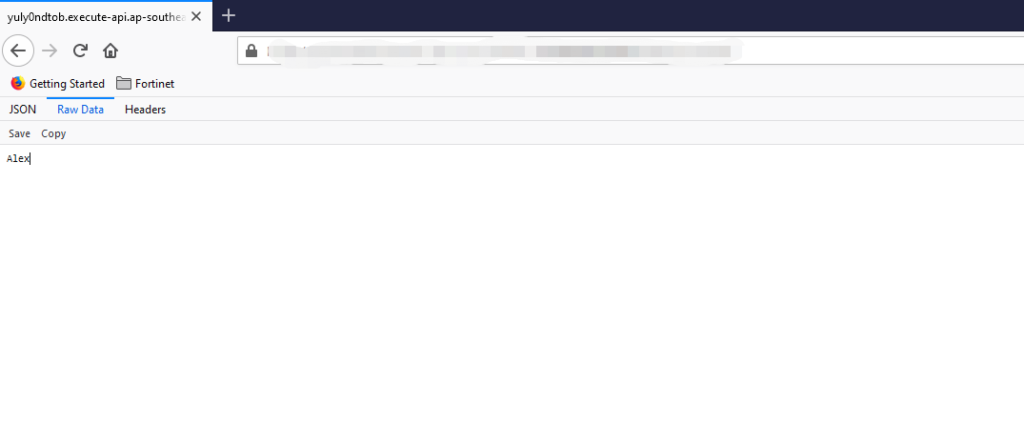
6. Test the function
Open the browser to test function just created.
You can reach out to us at- info@sprintnetworks.com, if you have any other questions or concern.