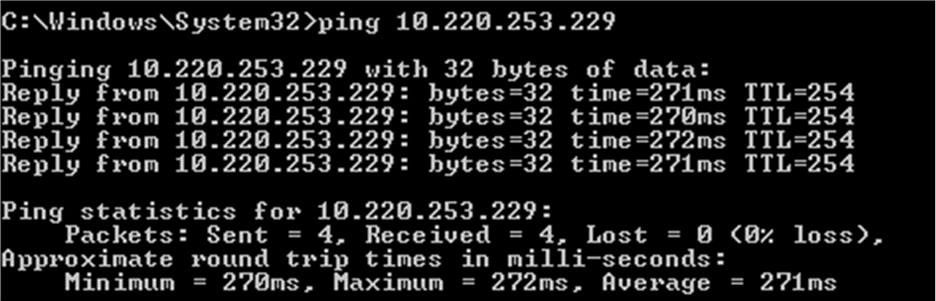
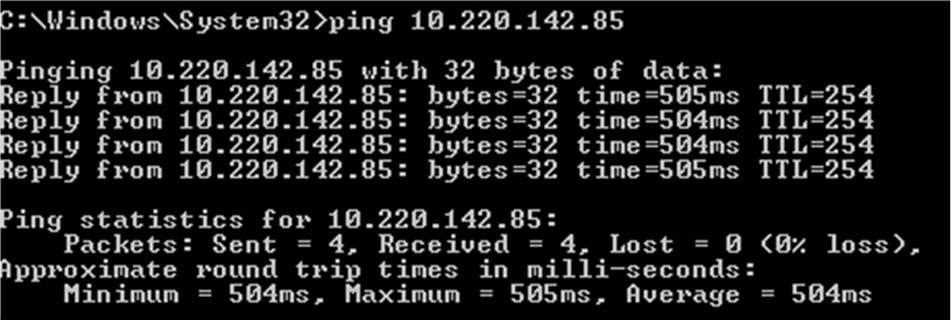
What should be expected from your threat intelligence?
Threat intelligence has been widely used right now, and it plays a crucial role in your security posture. If you are a cybersecurity professional, you must be familiar with the concept even though you might not fully understand how it works. It could be much more important to your various domains of cybersecurity, especially for those who are dealing with Security Information and Event Management tools or work within the incident response teams.
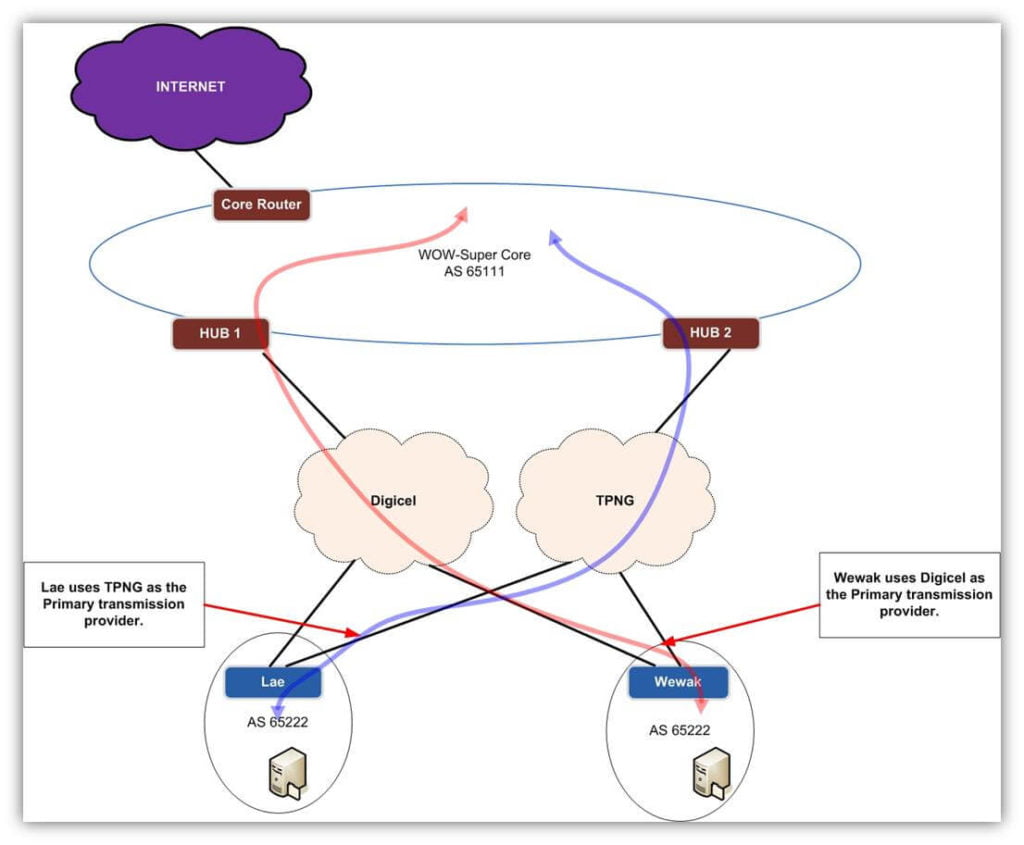
But, what you should be expecting when using a threat intelligence feed, especially when they need to collaborate with other security elements, such as NGFW, Email Services, WAF. Sprint Networks is partner with the leading security threat intelligence provider, Fortinet. What you should be expecting from the threat intelligence:
1. Antivirus:
2. Intrusion Prevention (IPS):
3. Application Control:

4. Security Rating Service:
5. IoT Service:
6. Indicators of Compromise (IOC) :
7. Vulnerability Scan
8. Web Application Firewall (WAF):
9. Web Filtering:
10. Industrial Control Systems Security: