Most Pacific Networks Does NOT conform to Best Practice Network Design! They lack Stability and Security. In this article, we share how you can design your Network for optimal performance in a typical Hub and Spoke Architecture. You can use these design strategies as a blueprint in your Data Network for TPNG or Digicel provided transmission.A stable, secure and high-performing data network is essential if organisations are to operate efficiently and provide customers, partners and staff members with an enjoyable user experience. By ensuring the network that delivers data, business applications and collaboration systems are robust, Stable, Secure, Scalable and reliable; organisations can increase productivity, enhance user satisfaction and keep costs down.
So What Are The Steps Required To Build Such A Networlk
Although we work with multiple ISPs in PNG; this article has no affiliation to any ISP in PNG. The content in this document is generic and meant to be used ONLY as a guide for building best practice WAN networks.
Consider The Following Case Study:
Customer “WOW-Super” is a new superannuation company in PNG. They are building their local presence by standing up two branches in Wewak and Lae, while the head office is located in Boroko. They have intentions to have wider coverage and expand in the future.The senior management team have contracted a reputable IT firm to design and build their WAN Data Network using best practice data solutions.
Scope Based On Customer Requirements
Build a state-of-the-art WAN Data Network with the following considerations:
- Robust and stable using Dynamic Routing
- Use best practise security solutions
- Be able to scale and anticipate growth when new branches are added.
- WAN redundancy using two services providers (example: TPNG and Digicel).
- One service provider should be primary while the other is back up, with Automatic Failover and high availability
- All server connectivity and Internet access will be via the Hub router(s), except for specific servers sitting behind each branch, where optimal routing should be used.
- It has been deduced from the latency reports supplied by the two ISPs, the link at the branch in Lae has better response time over the TPNG transmission, while the link at Wewak has a better response over Digicel. (NOTE: currently TPNG uses satellite links in Wewak and has a latency of approximately 500 milliseconds; this is considerably higher than Digicel). Therefore, it is prudent to use TPNG as the primary link at Lae and Digicel as the back. And, Digicel as the primary supplier in Wewak and TPNG as the backup
- Proactive Network Monitoring and Manage the data network during business hours.
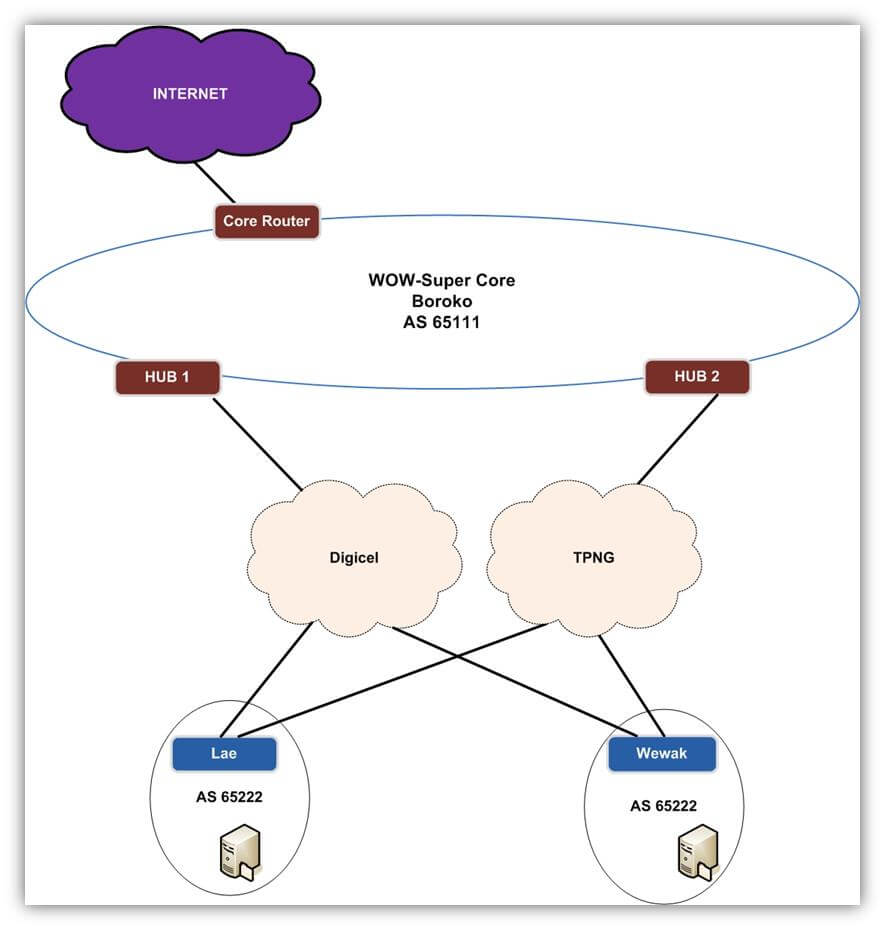
Figure 1: High-Level Design Overview
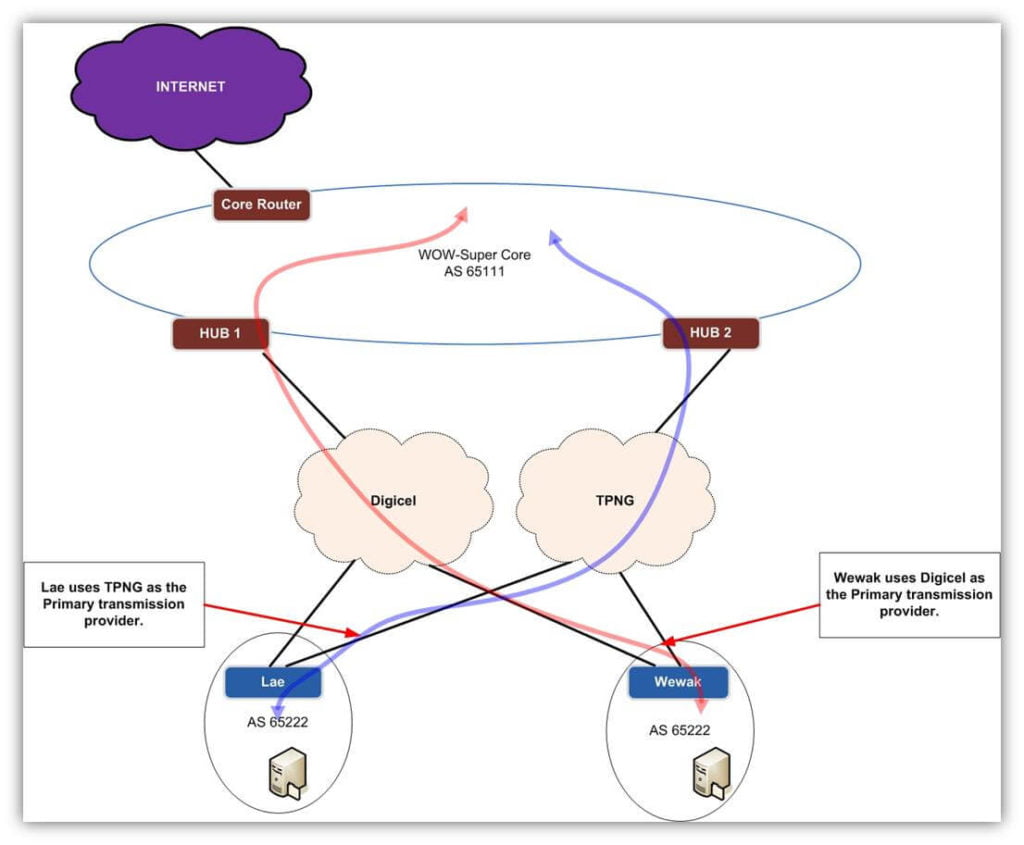
Figure 2: High-Level Design Traffic Flow
Note: WOW-Super already has a solid core network. That is, WOW-Super has used best-practise network solutions within their LAN architecture.Designing best practice LAN networks are not within the scope of this document. If you’re interested to learn how to “Designing best practice LAN networks” contact us today at info@sprintnetworks.com
ISP Offering
For TPNG:
The current TPNG offering is a flat layer 2 structure with VLAN based segregation for all WOW-Super braches (VPN based offerings are managed services offered by TPNG). Contiguous VLAN spaces for the branches are usually reserved.TPNG will provision pre-defined VLANs within its core and ensure data integrity and security is maintained. At the braches and at the hub, TPNG will present all ports as access-ports. You could also request Dot1Q tunnels to have aggregated links at the hub, but this could incur separate costs
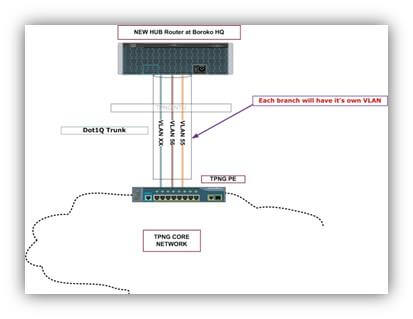
Figure 3: Possible Dot1Q aggregated Link at the hub
For Digicel
The Digicel network provides connectivity using RF communications from remote sites to a layer 2 backbone network used to interconnect all branches with the hub. Separations of customer networks are achieved through the use of Layer2 VLANs and Layer3 VPNs on the Digicel network. Digicel will provide a PPPoE transmission end-point at the customer CPE. These end-points will have layer 3 address forming point-to-point reachability. A pre-negotiated IP subnet will be used for Layer 3 communication. (we use 172.16.1.0/24)
The Approach
The goal is to have parallel networks over TPNG and Digicel. Therefore, the two service providers (Telikom PNG and Digicel) will provide data services via two (2) distinct networks. (refer to Figure 2 ).The Figure 2 illustrates the hub and spoke concept that is deployed over the two service providers’ networks. In order to maintain physical and logical separation, a new headend router for each service provider will be introduced at the customer HQ. These new routers will provide the added redundancy and the capability to run two data networks in parallel simultaneously. Thus, fulfilling one of the primary requirements set by the customer.Both Telikom PNG and Digicel will create a new VPN for the WOW-Super network to provide logical separation of WOW-Super traffic from other customers and the internet.NOTE: A pre-negotiated obligation of both ISPs should be to supply the following items listed below. It is, however, the responsibility of the customer/managed services provider to inquire about these items.
- Complete Layer 2 error report for both ISPs (BERT tests) and acceptable threshold
- Static IP allocation on the Client interface on the Digicel PPPoE links (reasons for this will be explained later in the document)
- Throughput tests should be performed by the customer end.
- Latency reports for Satellite links, fibre and radio links.
- Support contact details (this could be obvious but sometimes overlooked)
Some of these items could attract separate costs and therefore should be carefully assessed. This should be stipulated in writing and agreed by the customer, the ISP and the management services team. These items should be part of the ISP’s SLA agreement.
Here’s a summary of the functions that will be performed at both the hub (HQ) and each branch site for both services providers:
At the Head Office
Using TPNG
Installation and configuration of TPNG managed equipment and associated hardware into HQ. (TPNG responsibility)
Installation and configuration of WOW-Super managed equipment that will interface with the TPNG equipment. (WOW-Super responsibility)
Install and integrate the new head-end router PE1 into the WOW-Super network at HQ. This task would involve;
Enabling Layer 1/2 connectivity with SW1 and SW2 switches.
Integrating into OSPF Area 0
Enabling iBGP peering with the core layer devices at HQ.
Verifying that BGP route propagation is functioning as expected
Hub and branch routers have separate subnets for layer 3 connectivity;
Between the hub and branch, a DMVPN tunnel will be established These tunnels will be transparent to TPNG. Enable DMVPN in Phase 3, so that spoke-to-spoke communication is also possible.
Private Autonomous System Numbers (ASN) will be used;
Each branch will have an IPSec tunnel to the hub to secure the data plane, across the TPNG network that will be used to securely transport WOW-Super production traffic.
Over the IPSec tunnel an eBGP peering will be established
Using Digicel
Installation and configuration of Digicel managed equipment and associated hardware into HQ. (Digicel responsibility)
Installation and configuration of WOW-Super managed equipment that will interface with the Digicel equipment. (WOW-Super responsibility)
Install and integrate the new head-end router PE2 into the WOW-Super network at HQ. This task would involve;
- Enabling Layer 1/2 connectivity with SW1 and SW2 switches.
- Integrating into OSPF Area 0
- Enabling iBGP peering with the core layer devices at HQ.
- Verifying that BGP route propagation is functioning as expected
WOW-Super HQ site (Hub2) will be PPPoE clients and the Digicel edge router within the Digicel Core network will act as the PPPoE server;
The Digicel VPN PE routers will authenticate the PPPoE session using CHAP and pre-defined usernames and passwords. Authentication will occur against a centralised server within the Digicel network;
To provide point-to-point reachability between the PPPoE Dialler interfaces between the hub-site in Boroko and the branch sites eBGP will be used;
DMVPN tunnels will be established between the CPEs using the PPPoE Dialler interfaces as the endpoints (i.e. Tunnel source and destination). These tunnels will be transparent to Digicel;
IPSec tunnels will be built over the DMVPN tunnels using the recommended encryption policies for data security, encryption and decryption, also enable DMVPN in Phase 3;
eBGP peering between the CPEs across the IPSec tunnels will establish a secure data plane across the Digicel network that will be used to securely transport WOW-Super production traffic;
Private Autonomous System Numbers (ASN) will be used.
At Branch Offices
Using TPNG
Installation and configuration of TPNG managed equipment and associated hardware into each branch site. (TPNG responsibility)
Installation and configuration of WOW-Super managed equipment that will interface with the TPNG equipment. (WOW-Super responsibility)
Install and integrate the new branch routers into each WOW-Super branch network at Lae and Wewak. This connection can be performed on a collapsed distribution and access layer. This task would involve;
- Enabling Layer 1/2 connectivity with the branch switch(es).
Have a default-route from the branch network switches to the PE router.
The CPE at each branch will have an eBGP peering to the HQ Hub1;
The branches will have its own DMVPN tunnel towards Hub1 and an eBGP session will be established;
Using BGP preference, Hub1 will be preferred over Hbu2 as the primary traffic path for the branch at Lae to exit the local network;
Private Autonomous System Number (ASN) will be used;
Each branch will have an IPSec tunnel to the hub to secure the data plane, across the TPNG network that will be used to securely transport WOW-Super production traffic.
Using Digicel
Installation and configuration of TPNG managed equipment and associated hardware into each branch site. (Digicel responsibility)
Installation and configuration of WOW-Super managed equipment that will interface with the Digicel equipment. (WOW-Super responsibility)
Same router as the corresponding step will be used;
Similar PPPoE transmission connection will be performed as per the HQ, with CHAP as the authentication method;
The CPE at each branch will have an eBGP peering to the HQ Hub2;
The branches will have its own DMVPN tunnel towards Hub2 and an eBGP session will be established;
Using BGP preference, Hub2 will be the preferred for data traffic at Wewak and TPNG will be the secondary path;
Same Private Autonomous System Number (ASN) will be used;
Each branch will have an IPSec tunnel to the hub to secure the data plane, across the Digicel network that will be used to securely transport WOW-Super production traffic.

